xDefense
Know your risks to better protect your assets
THE CONTEXT
Up until the 2000s, industrial systems and networks were immune to cyber threats, they were not networked via IP addresses and mostly used proprietary protocols.
With Industry 4.0, all industrial plants, such as renewable power plants, energy dispatching stations and manufacturing plants, have been the protagonists of important changes.
The growing interconnection between industrial electronic devices and communication networks, exposes the industrial environment to the threats of cyberspace and companies to the potential risks of disruption as a result of cyber attacks.
Unsurprisingly, regulations mandating the critical national infrastructure’s adoption of security measures, capable of ensuring resilience of their provided services, have been enacted.
It’s crucial to know what to protect before you start protecting!
For years, Vendors has been the only ones that know the characteristics of assets in the industrial sites. This lack of visibility on where these critical assets reside naturally leads to an inability to protect the same assets.
Asset visibility is the starting point for any security activity, therefore, Bip CyberSec has developed a significant proven methodology to carry out the Technical Inventory activity.
Therefore, how do organisations improve visibility of their assets and so help ensure resilience and regulatory compliance within the critical infrastructure sector?
THE PRODUCT
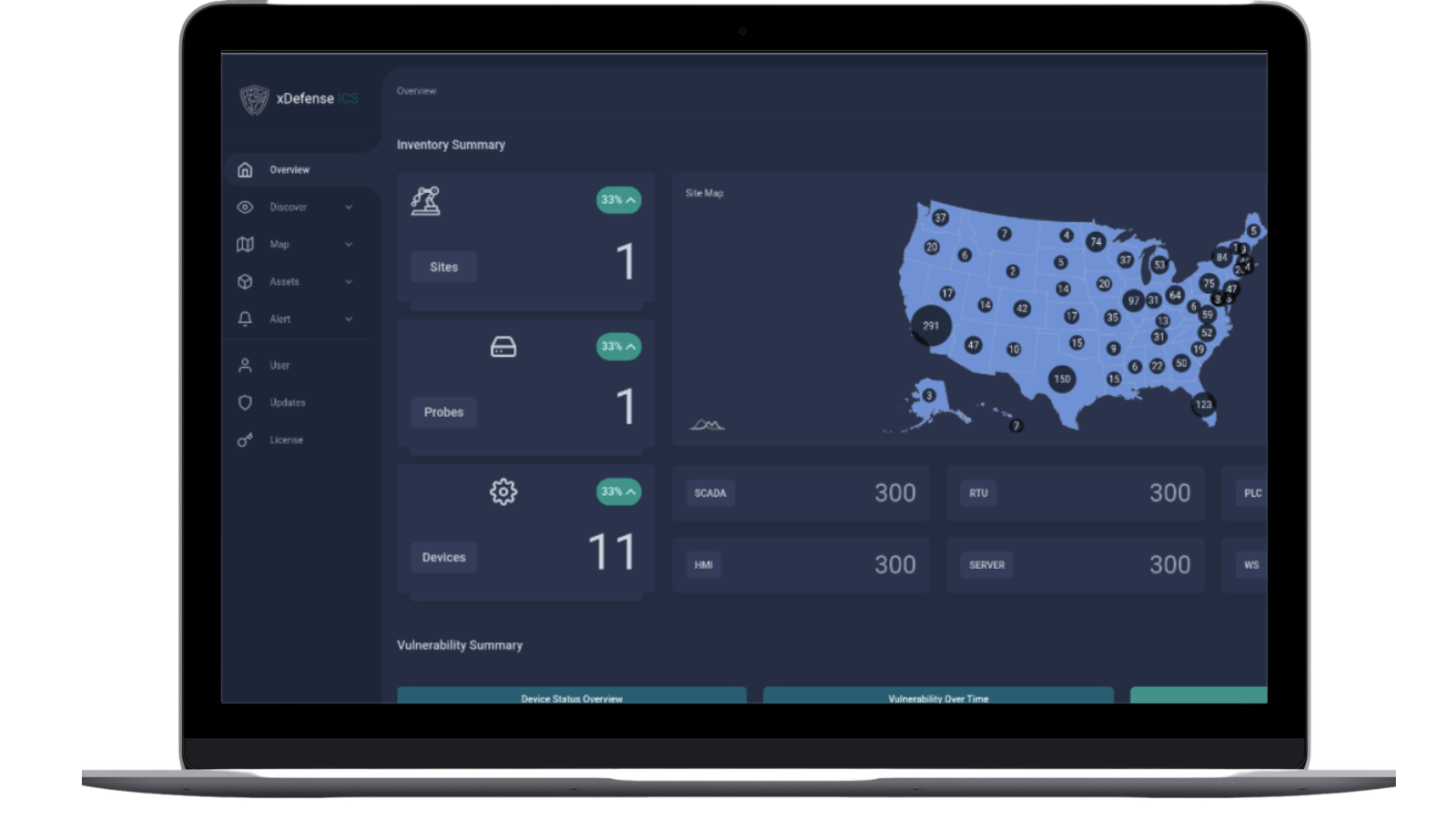
xDefense is the BIP CyberSec solution to increase visibility of assets, asset configuration and communication flows which provides organisations with a deep knowledge of their technological OT critical infrastructure.
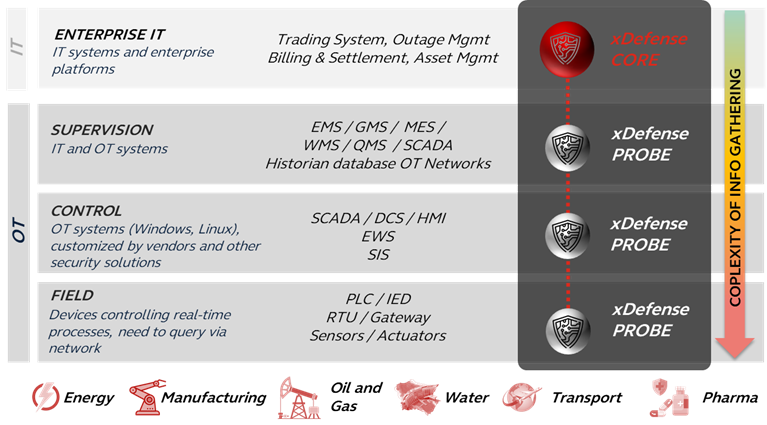
xDefense is a scalable solution based on a client-server architecture, composed of:
- xDefense CORE: the “heart” of the entire platform, stores data arriving from the probes and provides through an innovative GUI analysis and reporting features. This component can act as data broker between other data sources and enterprise asset management systems
- xDefense PROBEs: these are responsible for discovering the OT assets and collecting information without impact to normal operations. Based on the collecting techniques, they can be agentless or agent based.
With xDefense:
Know your environment, collecting detailed info, as HW/SW/NW (vendor agnostic), from main industrial assets, the OT asset management is fed.
Security processes are supported, under patch management and Incident Response, by virtue of:
- Security report generation
- Not needing to send sensitive information via e-mail
- Ability to manage vulnerabilities within their lifecycle
- Consolidation of different activities in a single place
- Validation Cyber Security Perimeter
- Interfacing external CMDB
Know your-risks, through the correlation of inventory with vulnerabilities, a unique view of the OT security and risk status is provided.
Key features
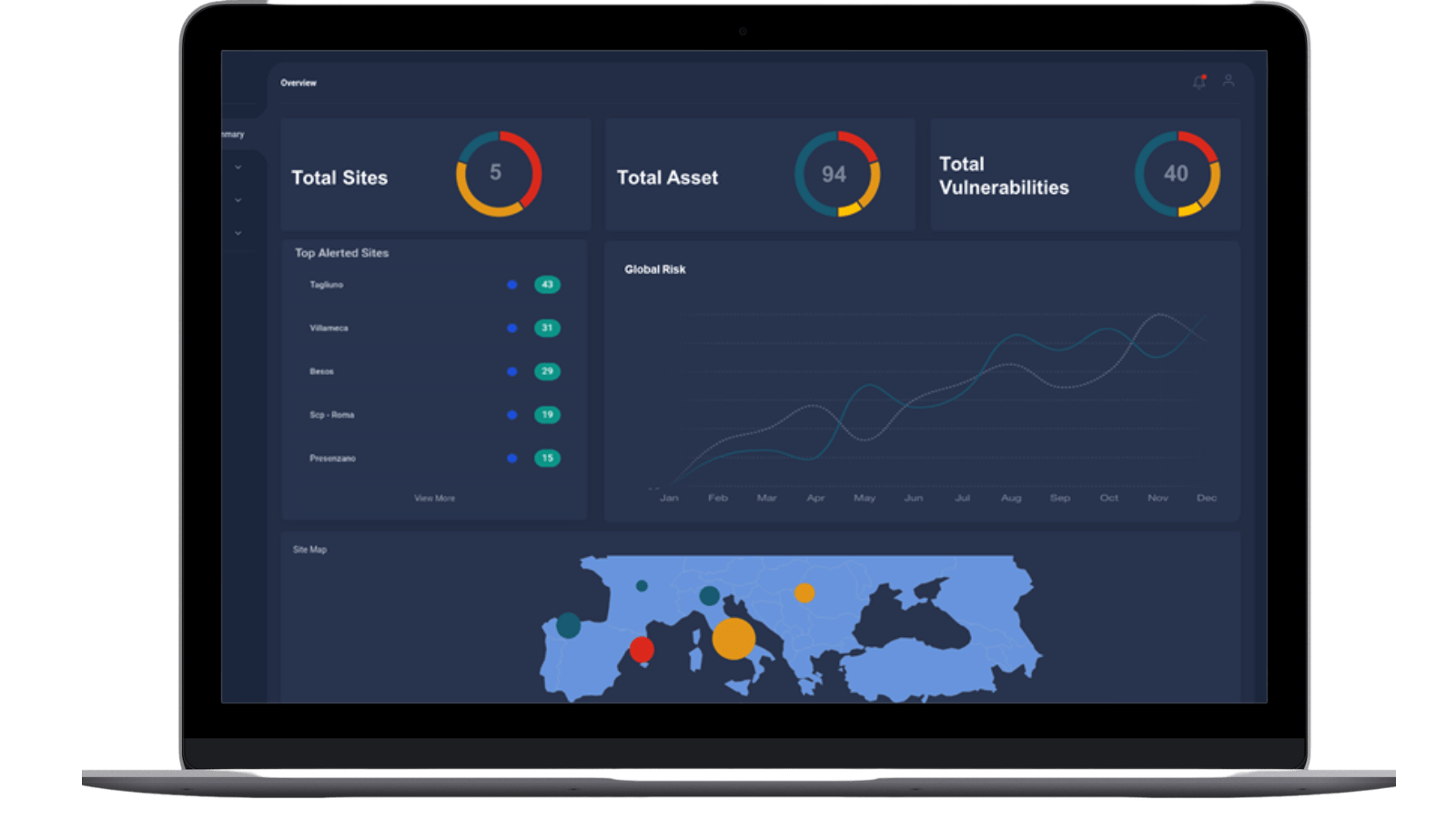
Executive view
Know your industrial environment security status
The executive view equips C-levels with a one dashboard report providing insight to all the main indicators of the security status of their industrial environment. This view enables the identification of critical issues and prioritises the required actions throughout the period that the global risk level is assessed and monitored.
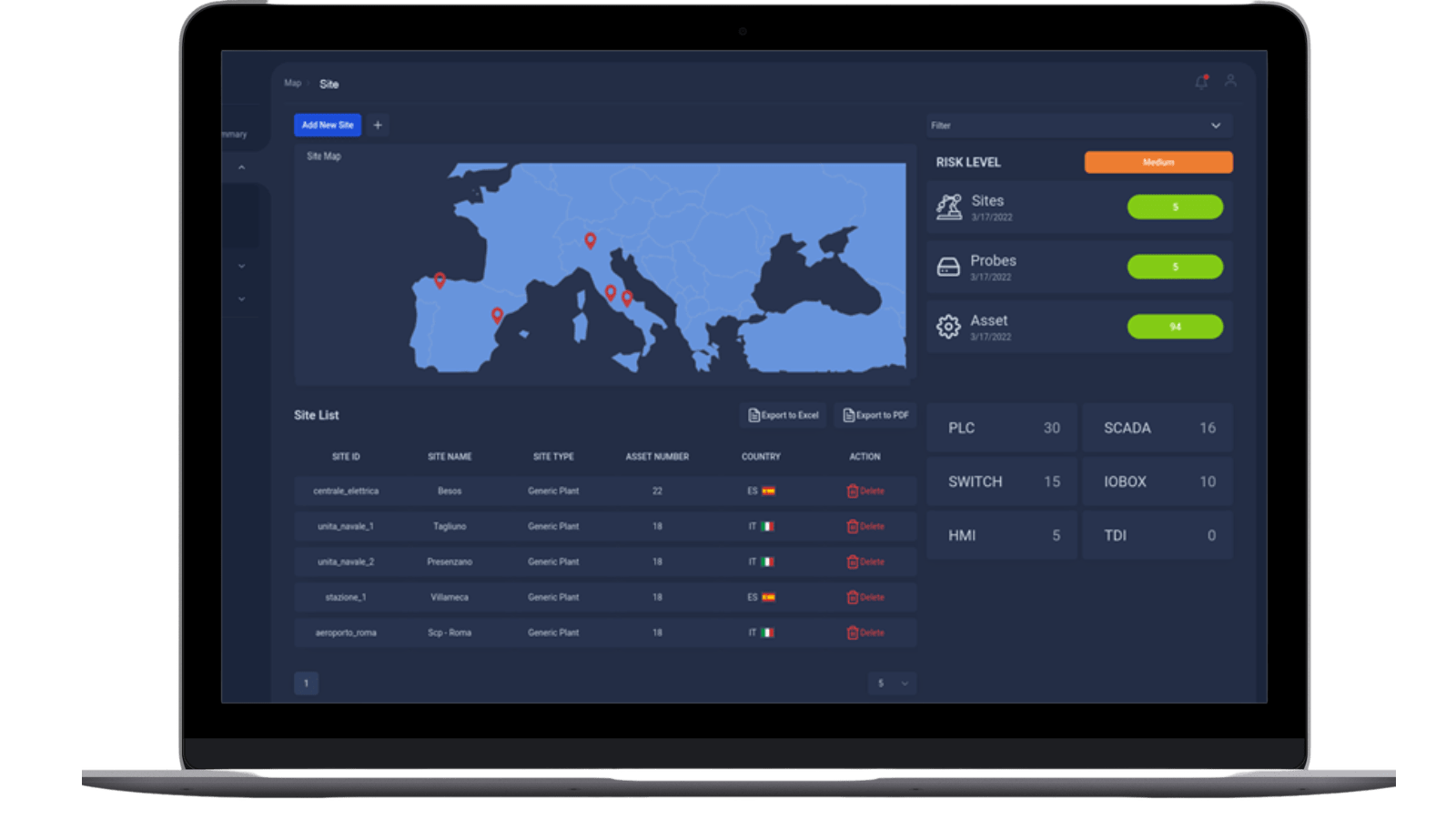
Indeed, each site has a risk levels indicator in the range from Low to High which simultaneously assess the criticality of the site itself and the actual risk exposure due to the presence of vulnerabilities on assets, weight for their severity. This indicator depicts a continuously up-to-date snapshot of the discovery of new assets and vulnerabilities.
Discover
Collect information to build a detailed baseline inventory
The automatic discovery of industrial assets accelerates and improves OT visibility capabilities uncovering the smallest details of the production infrastructure.
The main features are related to:
Construction of detailed baseline inventory
- Data collected gives access to useful information: IPs and MAC addresses, serial numbers, device types, vendor references, OS, firmware and hardware versions, serial numbers, etc.
Scalable solution based on a client-server architecture, consisting of:
- A core platform: stores data coming from the probes and provides the user interface, analytics, analysis, reporting features
- A Probe: installed directly in the industrial sites, performs inspections of assets; it could be agent based or agentless
The key benefits are:
- Up to date asset inventory
- Scalable and flexible solution
- Active and/or passive collection
- Agent less and/or agent based probes
Explore
Innovative web GUI and ad hoc query tool to easy navigate data
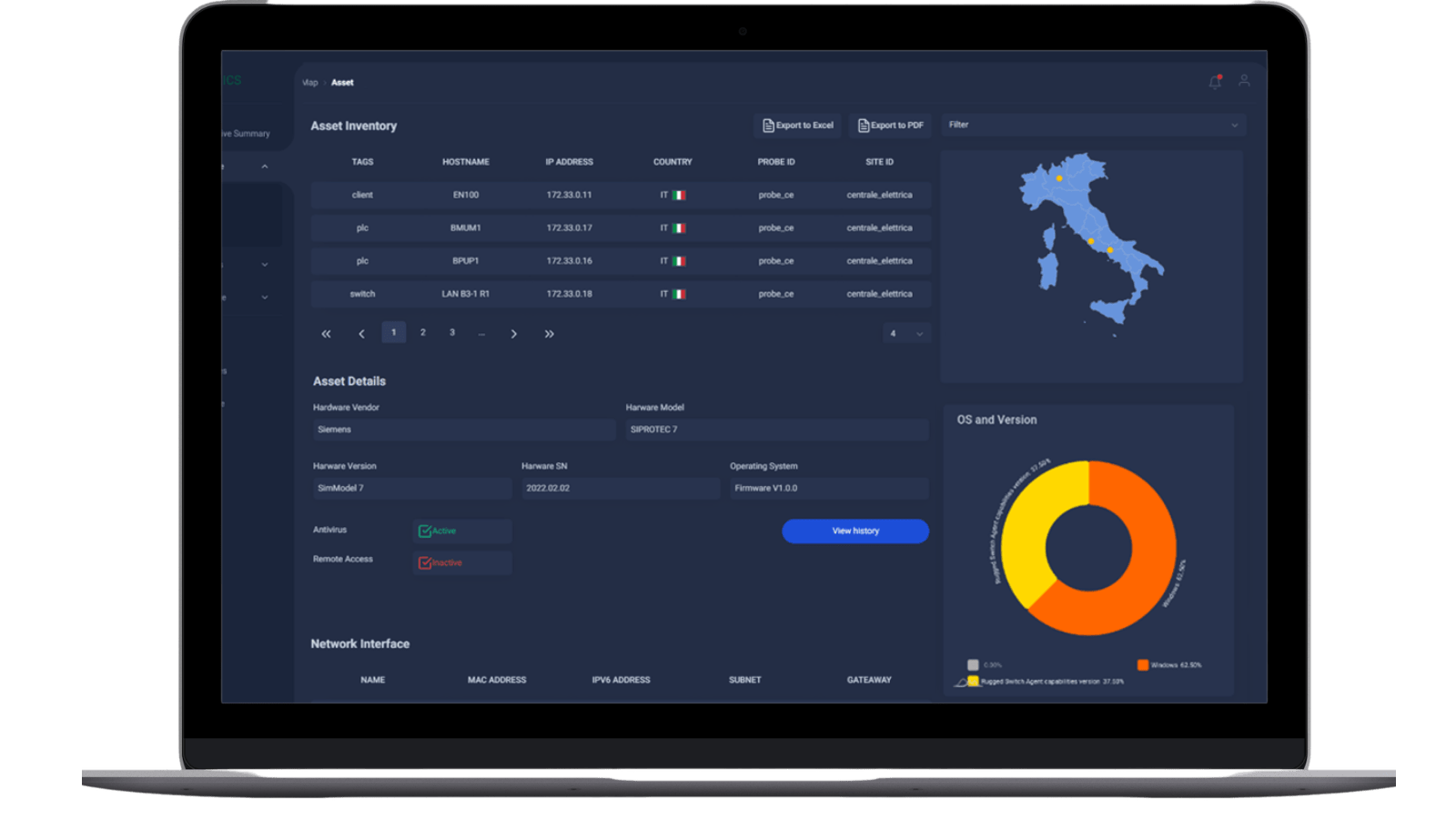
The platform gives the OT teams the possibility to explore in a centralised way the industrial network as composed by assets distributed across several countries in many industrial sites. An innovative Web GUI allows the navigation of all data relating to industrial systems through.
The solution provides a hierarchical inventory for an easy navigation of information. Navigation starts from a geographical map. Users can identify a specific site and drill-down to a point of singularity and discover all its resources, by browsing for details, as well as potential open systems’ vulnerabilities. In particular, it is possible to:
- Data drill down on site, network and asset details
- View network topologies and asset relationships
- Add tags to cluster assets in accordance with business needs
- Design dashboard with different views
- Filter data using a powerful ad hoc query tool to provide fast and effective reporting, analysis and overviews

Asses
Eyes on vulnerabilities to a prompt remediation for containing risk exposure
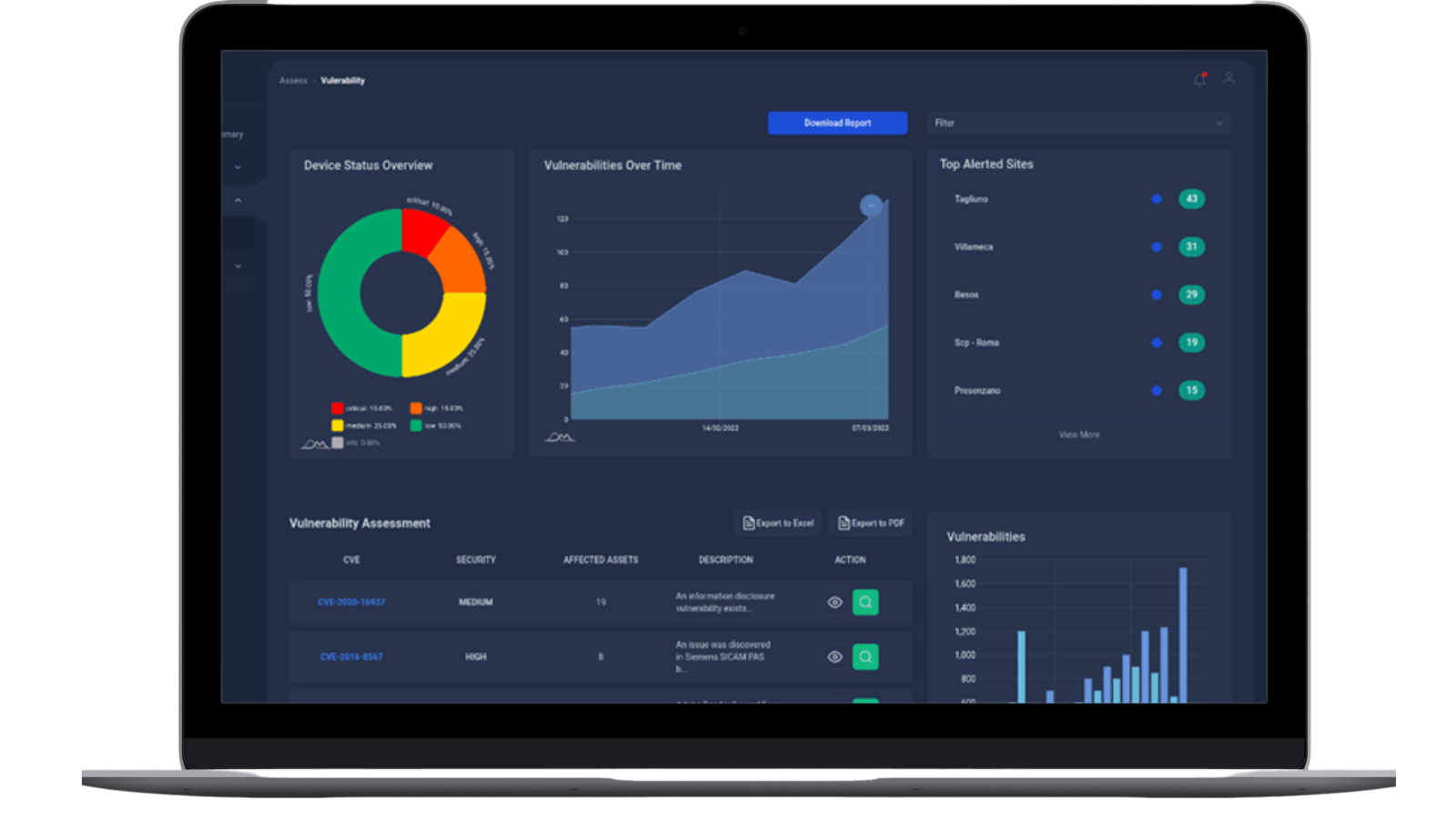
The Assessment platform capabilities detect systems exposed to known vulnerabilities, supports the vulnerability identification processes, is non-impacting to day-to-day operation(s) and enables rapid responses to contain risk exposure.
This feature is embedded in the xDefense Core which contains a correlation engine to relate information concerning system configurations and installed programs with known vulnerabilities as reported on public lists.
Through an intuitive dashboard it is possible to access all details such as, for example, vulnerability name, description and standard scoring. This allows for the identification of critical vulnerabilities which supports prompt remediation actions.
Are you interested?
Fill in the form and you’ll be contacted by our experts!