Privacy DIVE
Your personal data cockpit
THE CONTEXT
Privacy DIVE is our software designed to offer valid support in complying with obligations introduced by EU Regulation on personal data protection (GDPR) to both public and private organisations. Privacy DIVE is available on the Cloud, offered with a Software as a Service model, and in a variety of languages (e.g., English, French, Italian).
THE PRODUCT
Through a step-by-step procedure, the user is guided to complete the following requirements:
Identify all the personal data processed and fulfill the “Record of processing activities”;
Select the (technical and organisational) countermeasures to lower risks;
Manage all the privacy documentation and potential Data Breaches communications.
By leveraging Privacy DIVE, organisations will also be able to safeguard their employees’ privacy in the smart and remote working era and in anticipation of future disruptive events.
Key features
Foundational Module
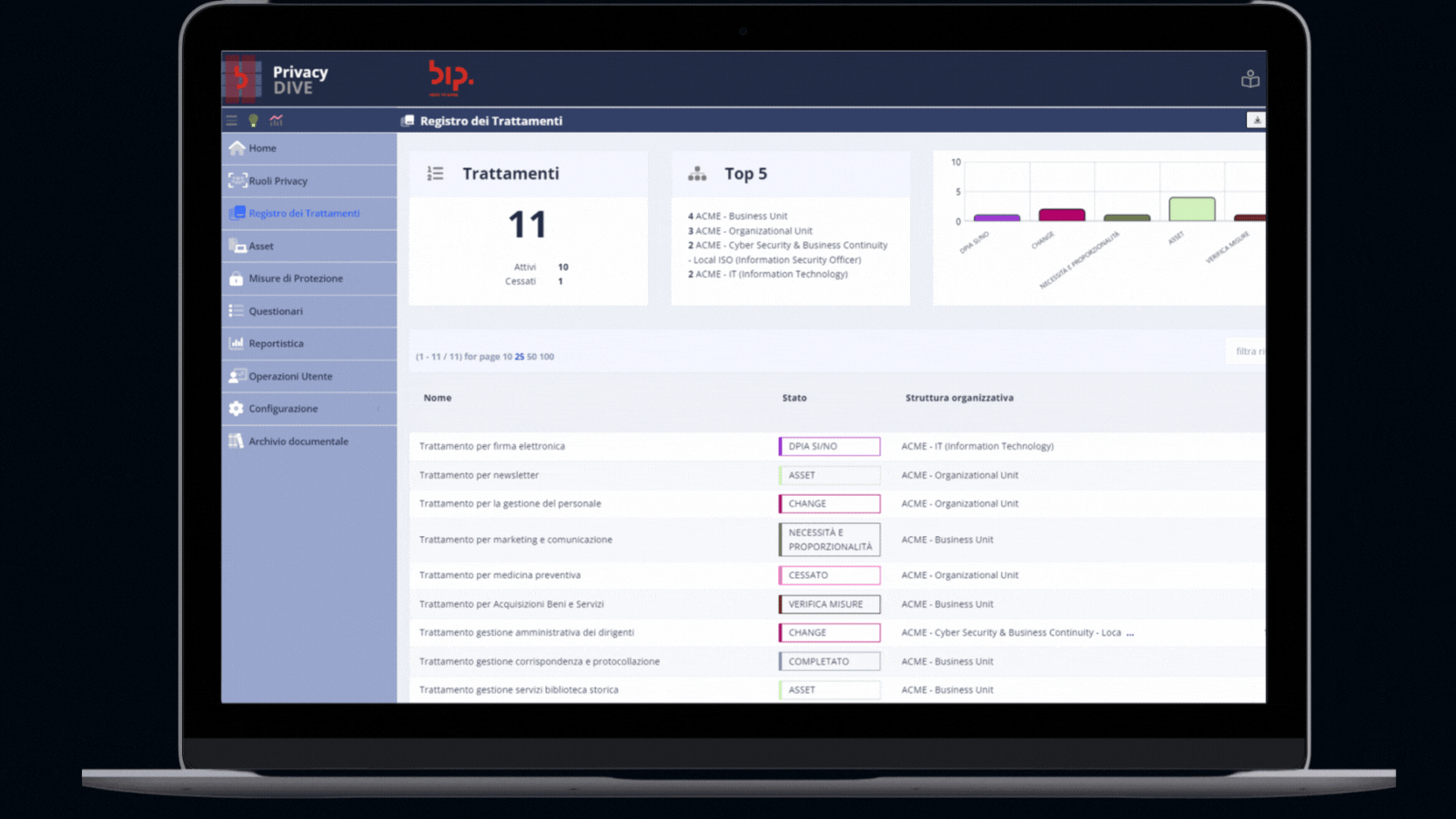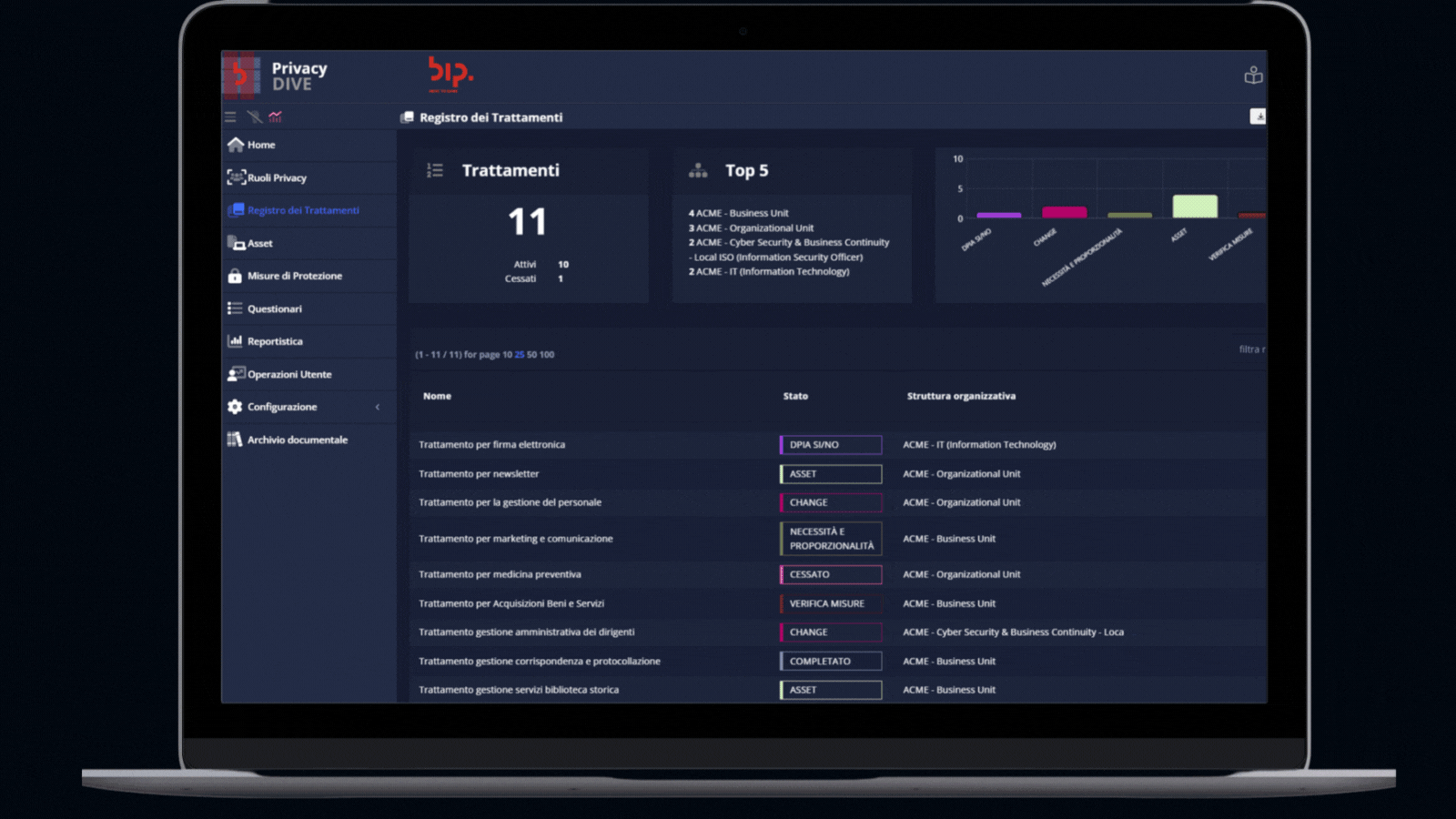
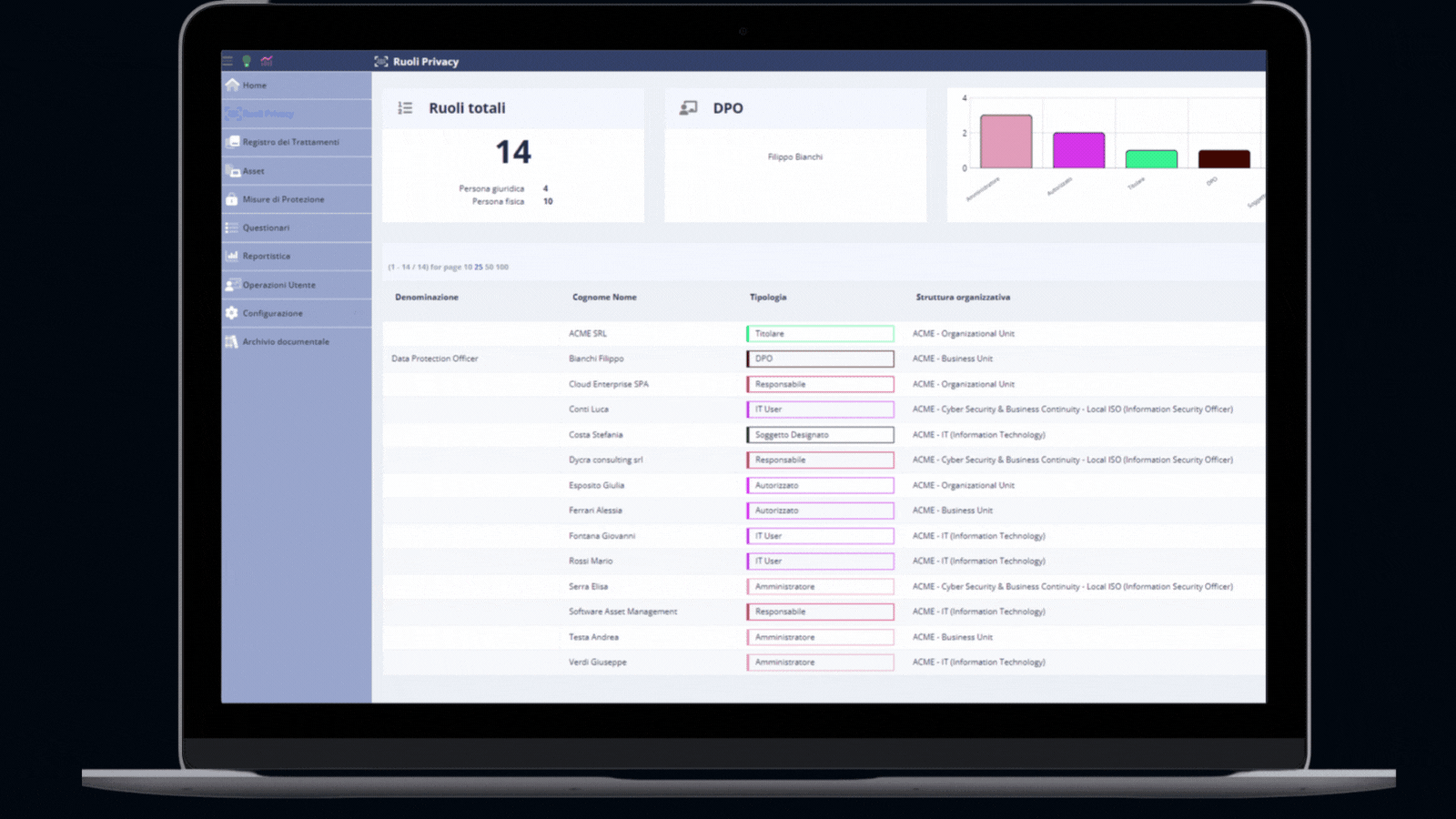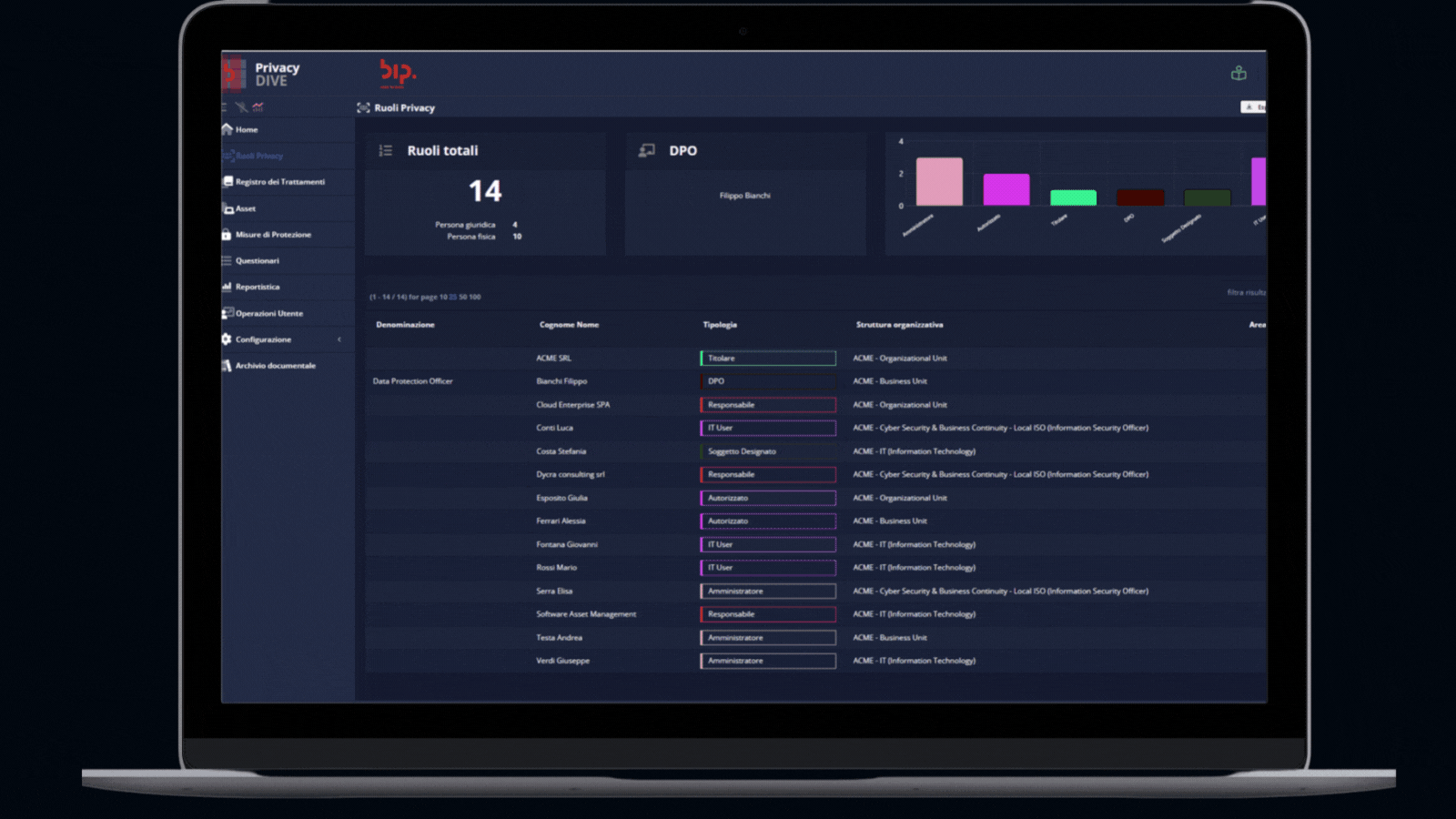
Record of processing activities
Our main module enables organisations to create a centralised inventory of processing activities, for which the Data Controller is accountable, and keep it up to date and aligned with new data processed.
DPIA/DPRA Module
Selection of security measures and risks mitigation plan
This extended module includes:
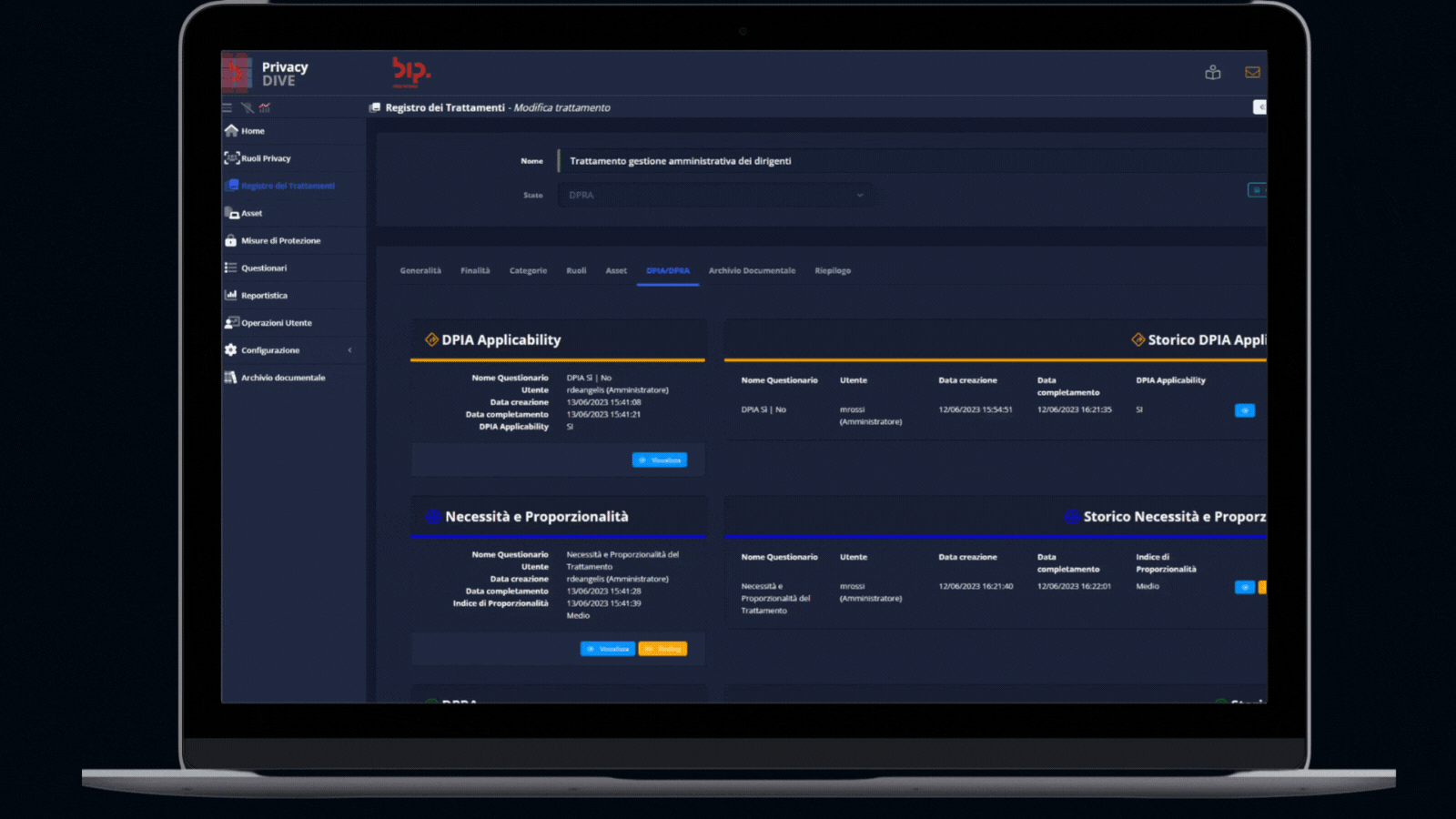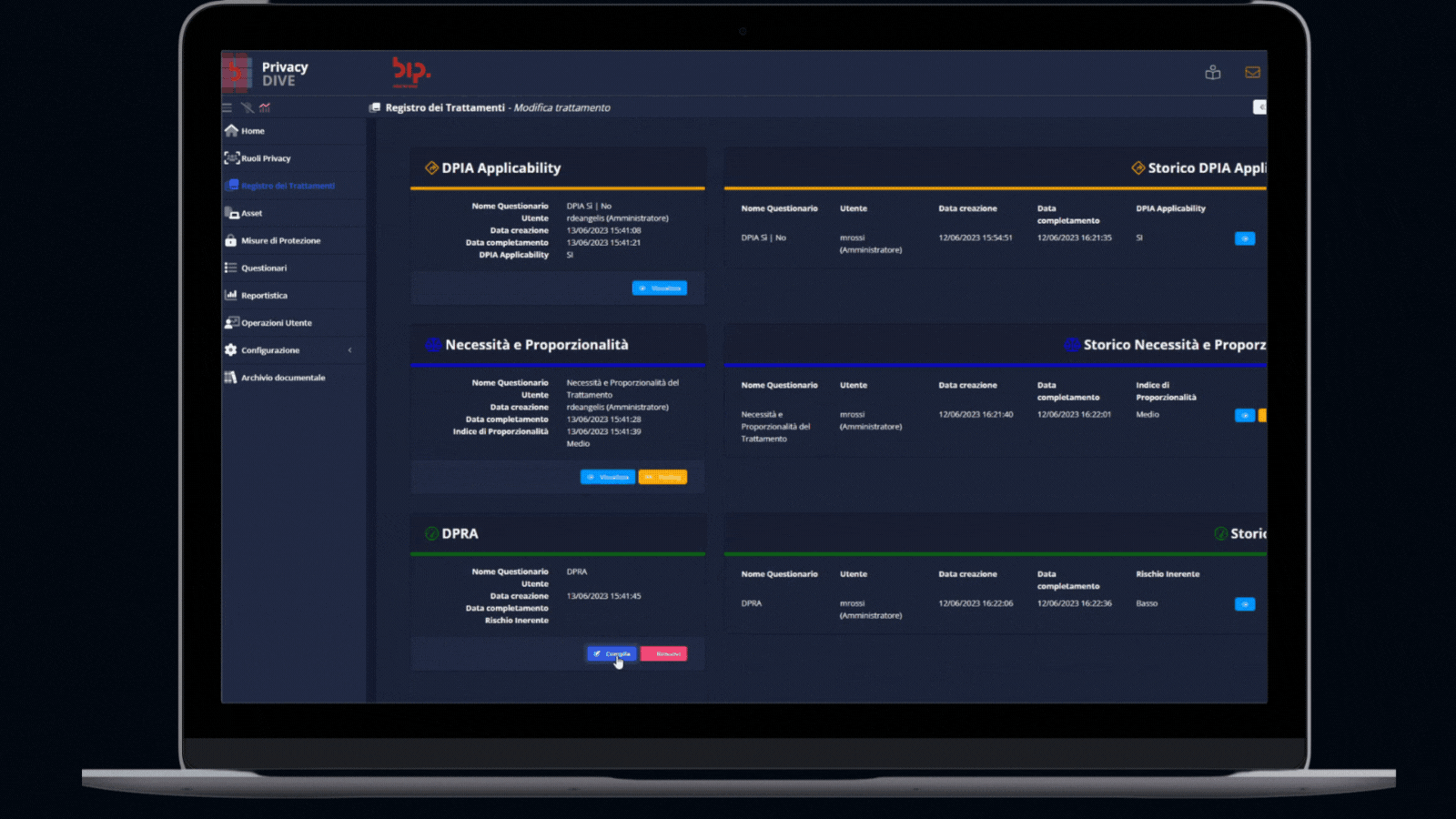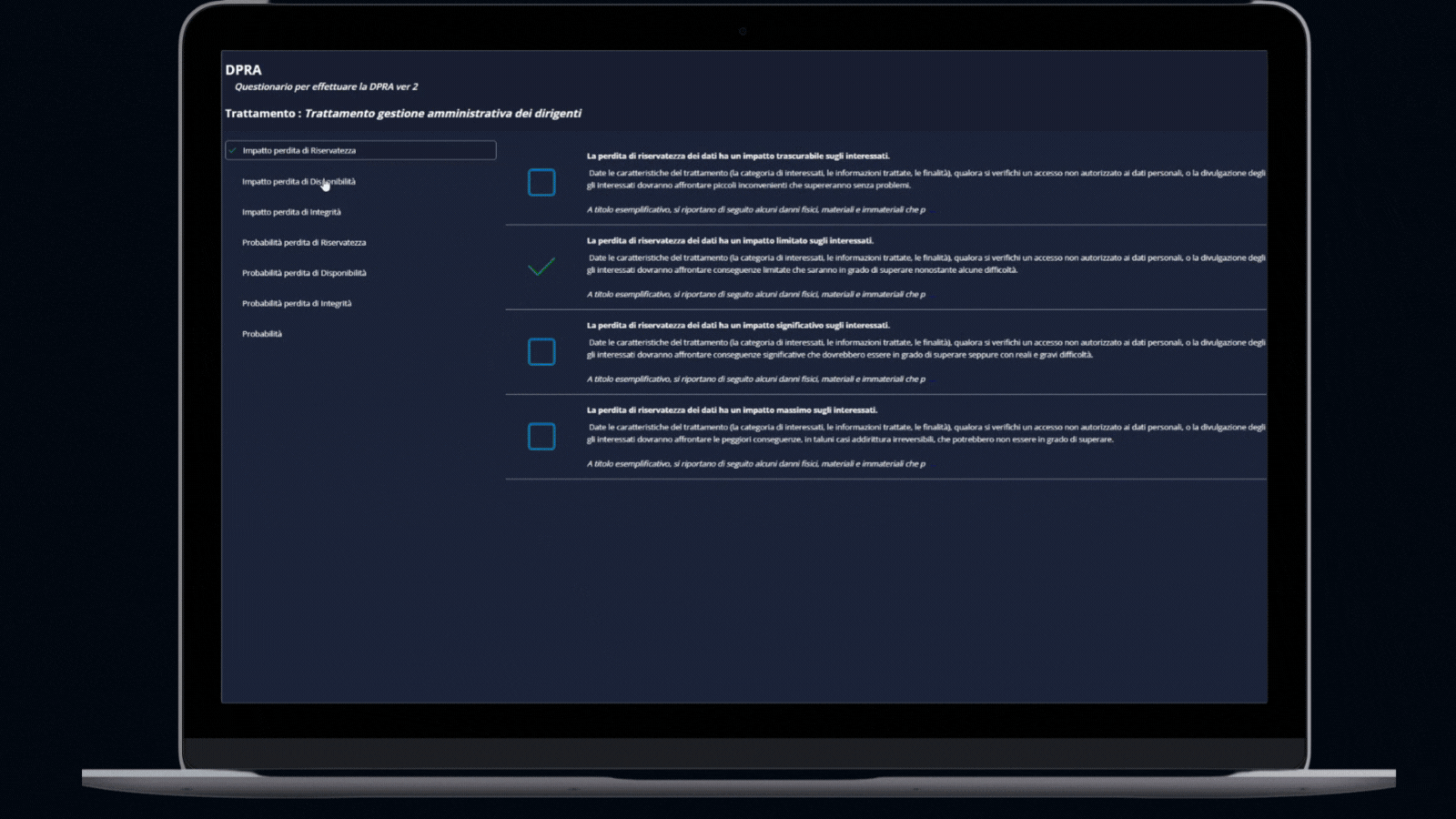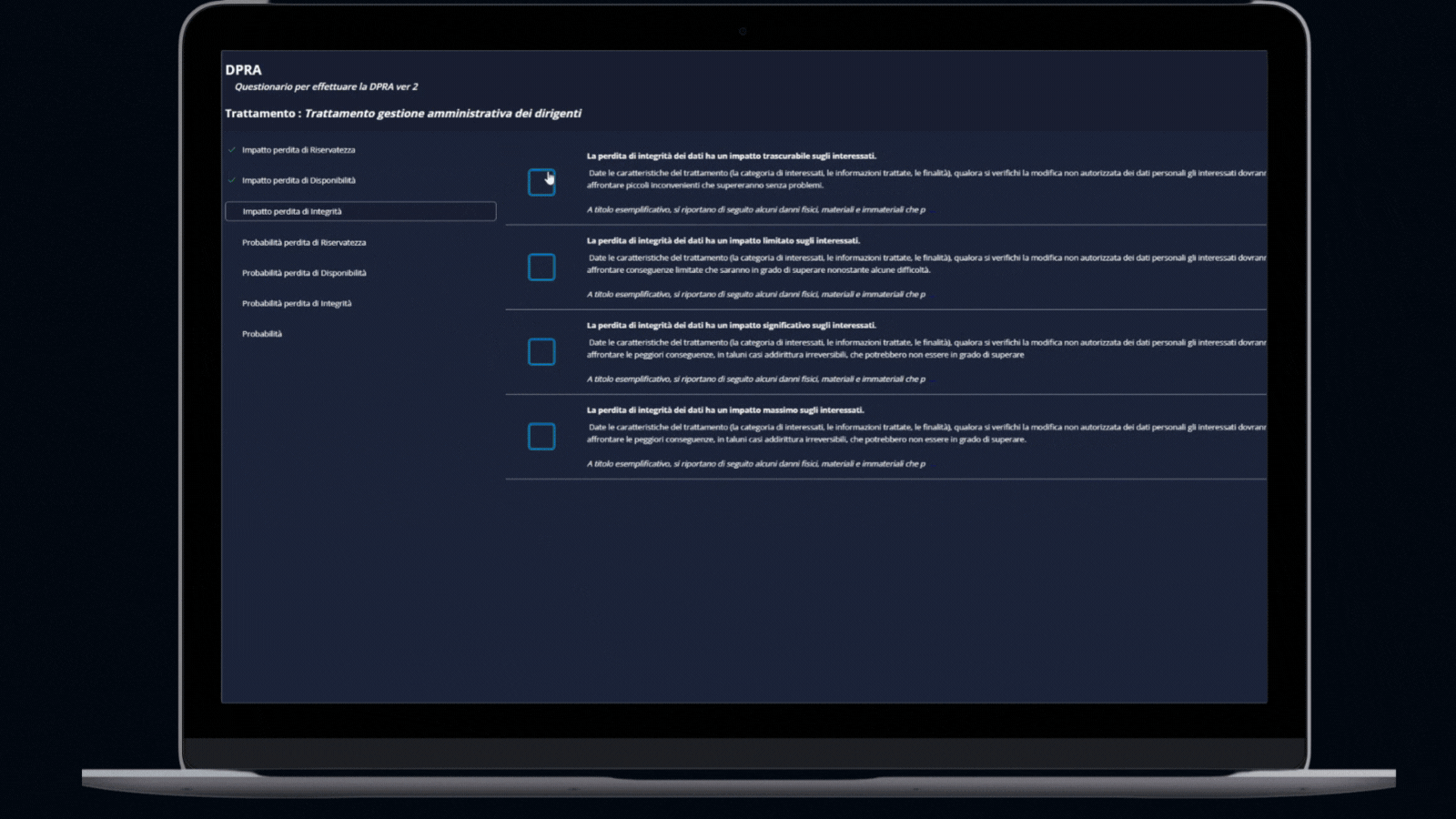
- DPIA: Checklist gathered from best-practices to perform a Data Protection Impact Assessment.
- DPRA: Methodology for the evaluation of the freedom and rights of the data subject, beyond the risk likelihood and potential impact.
- Gap Analysis between inherent risks and organizational/technical countermeasures implemented on every asset.
Document Management Module
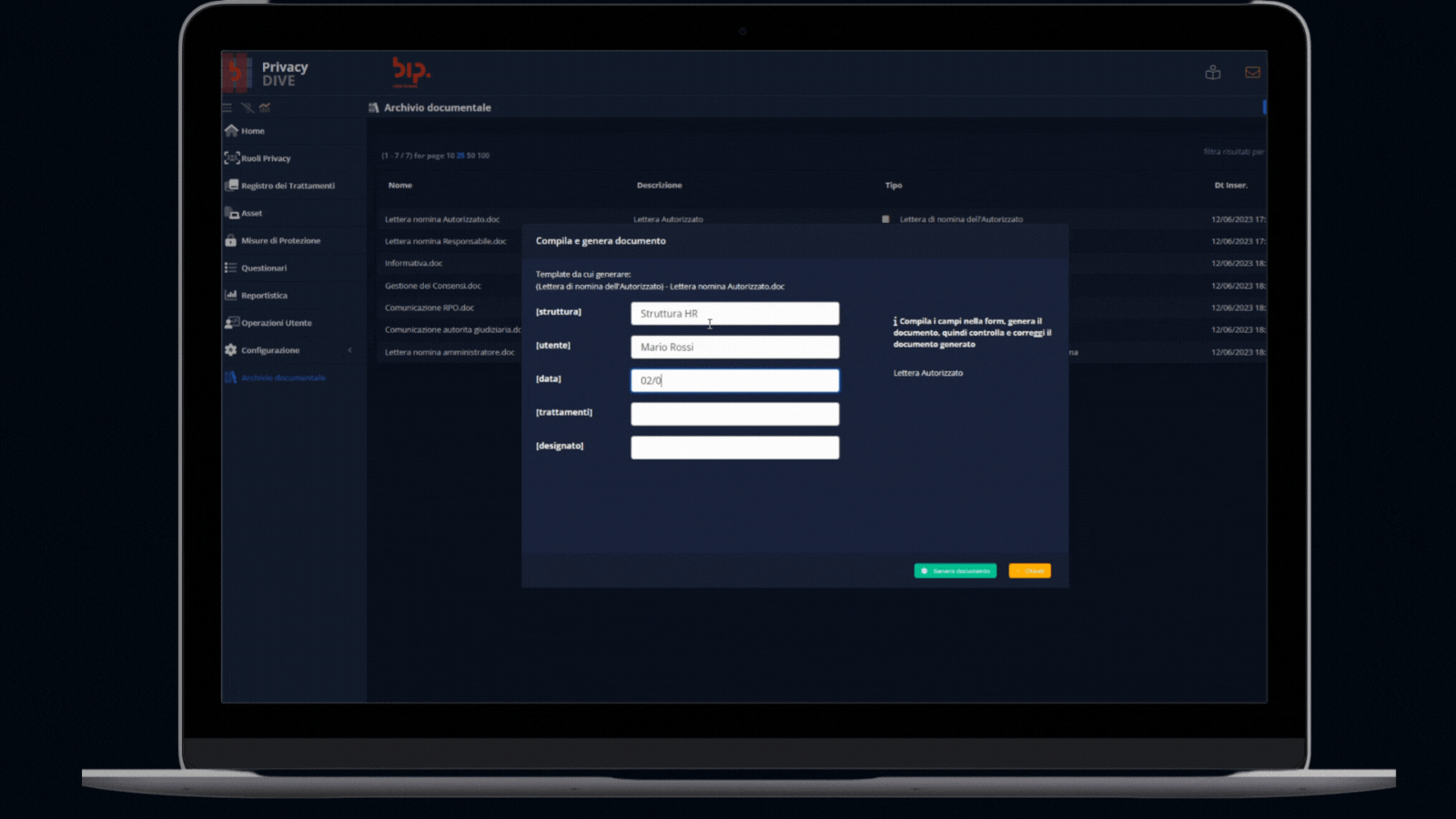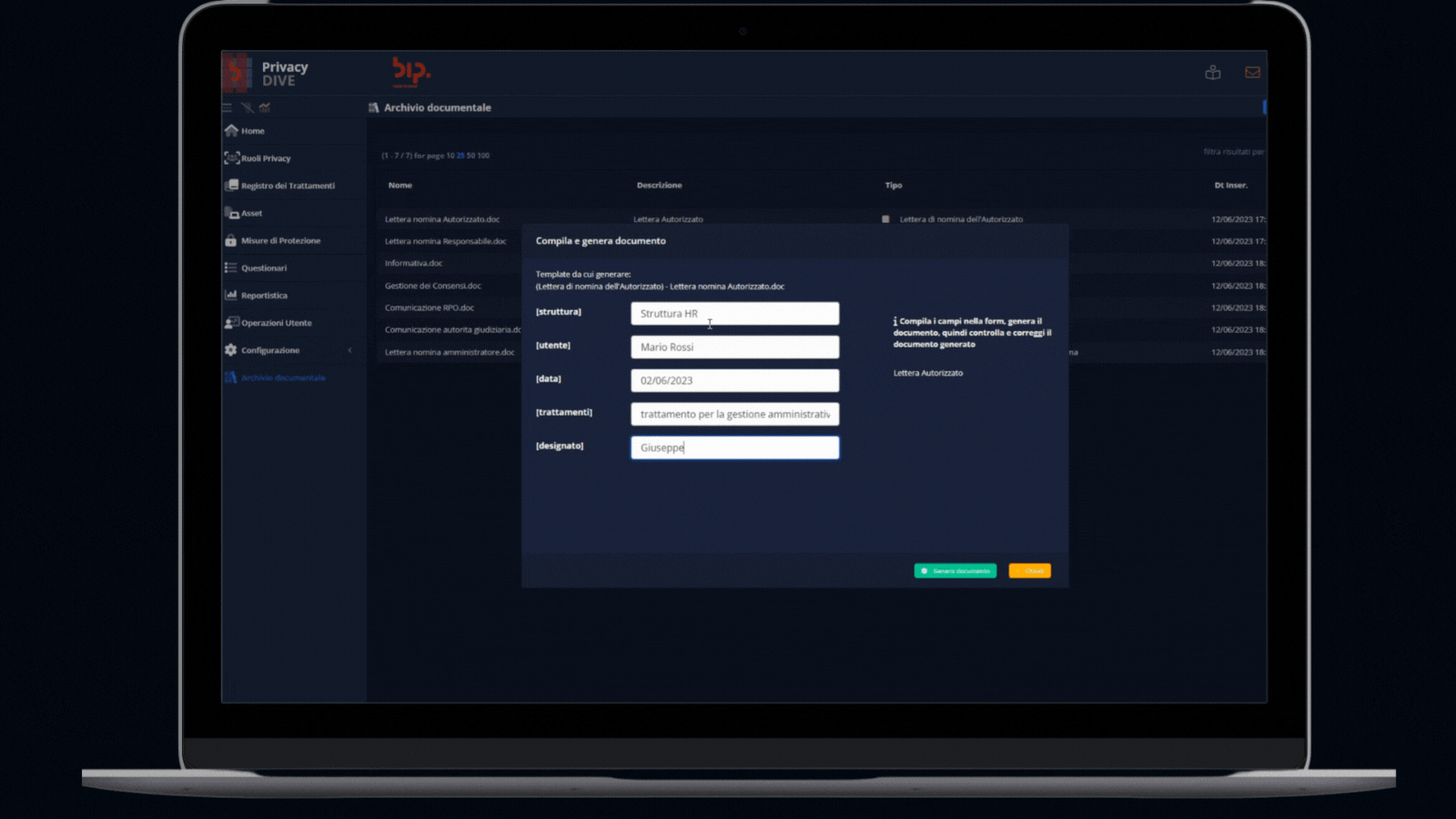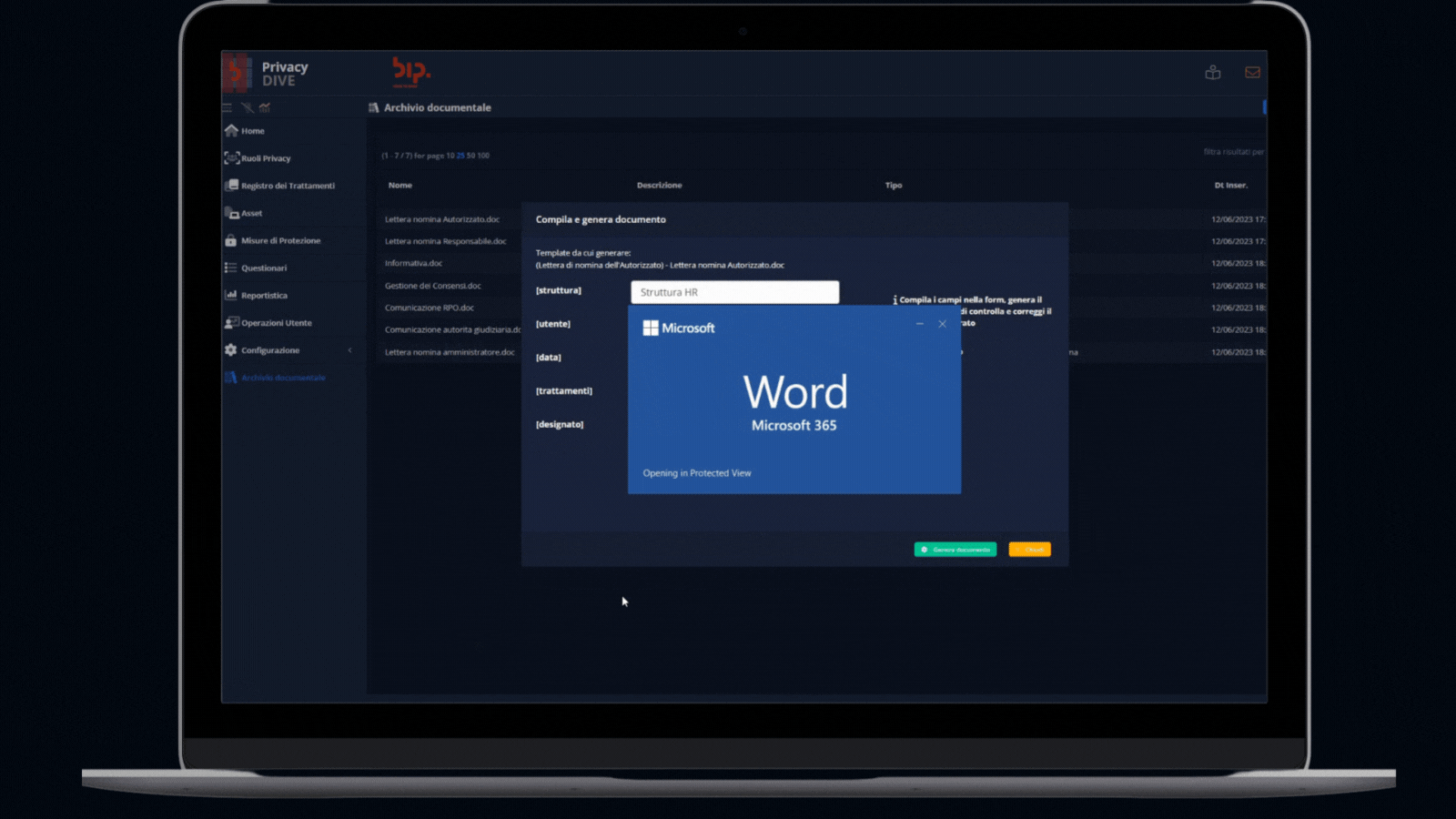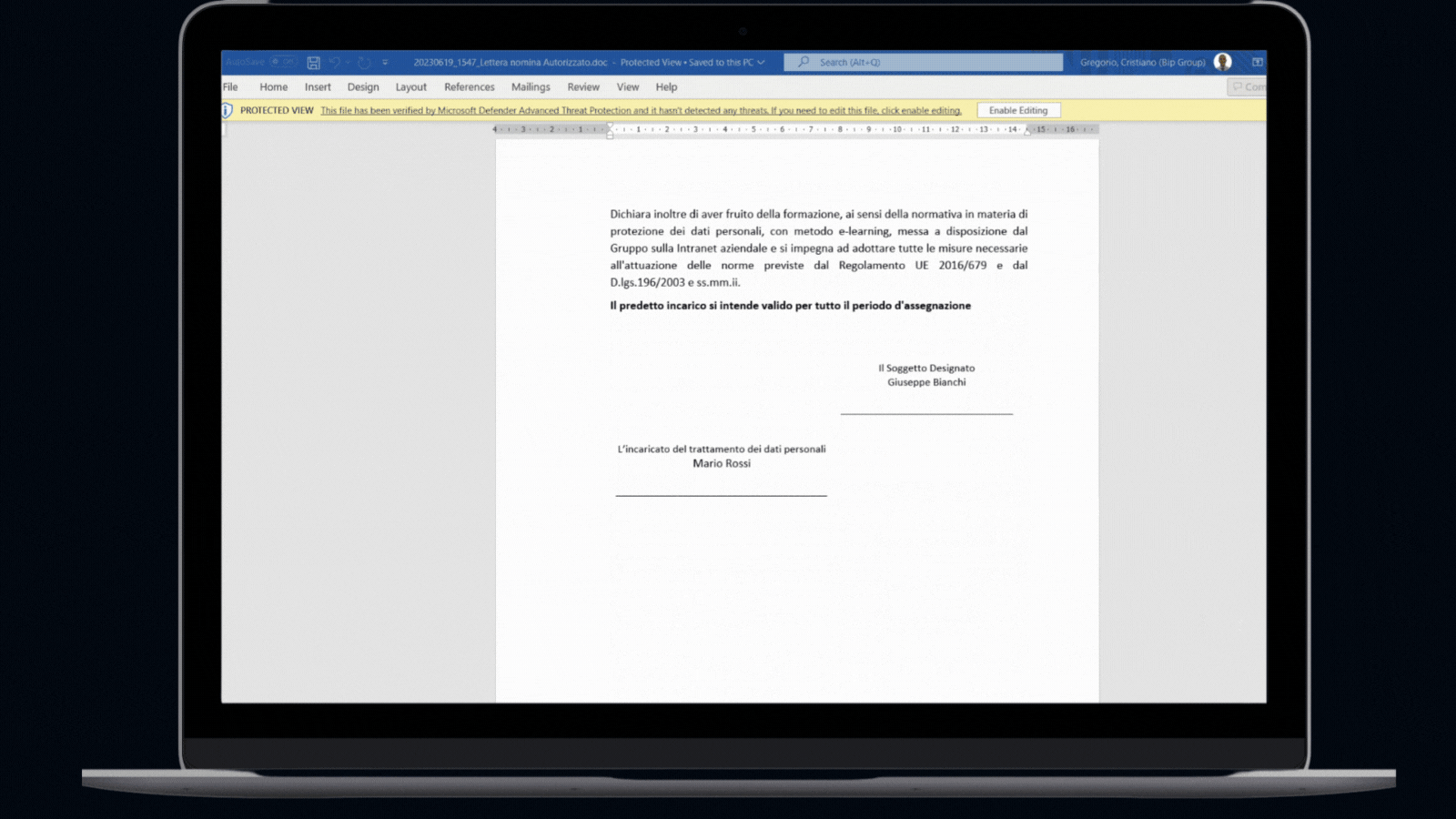
Drafting and storaging of privacy documentation
This extended module allows to create and manage all the privacy documentation related to the activities processed (e.g., consent, processor engagement) or other regulation requirements (e.g., communications to DPO or Supervisory Authorities).
Role Management Module
Simplify your user management tool
Our user information management form comes equipped with registration, access, and profile management features, all presented through an intuitive interface. Our platform provides efficient user management solutions through activity monitoring, report generation, and automated administrative processes. Our service provides seamless integration with Azure AD to ensure smooth authentication and authorization processes for your organization.
Report Module
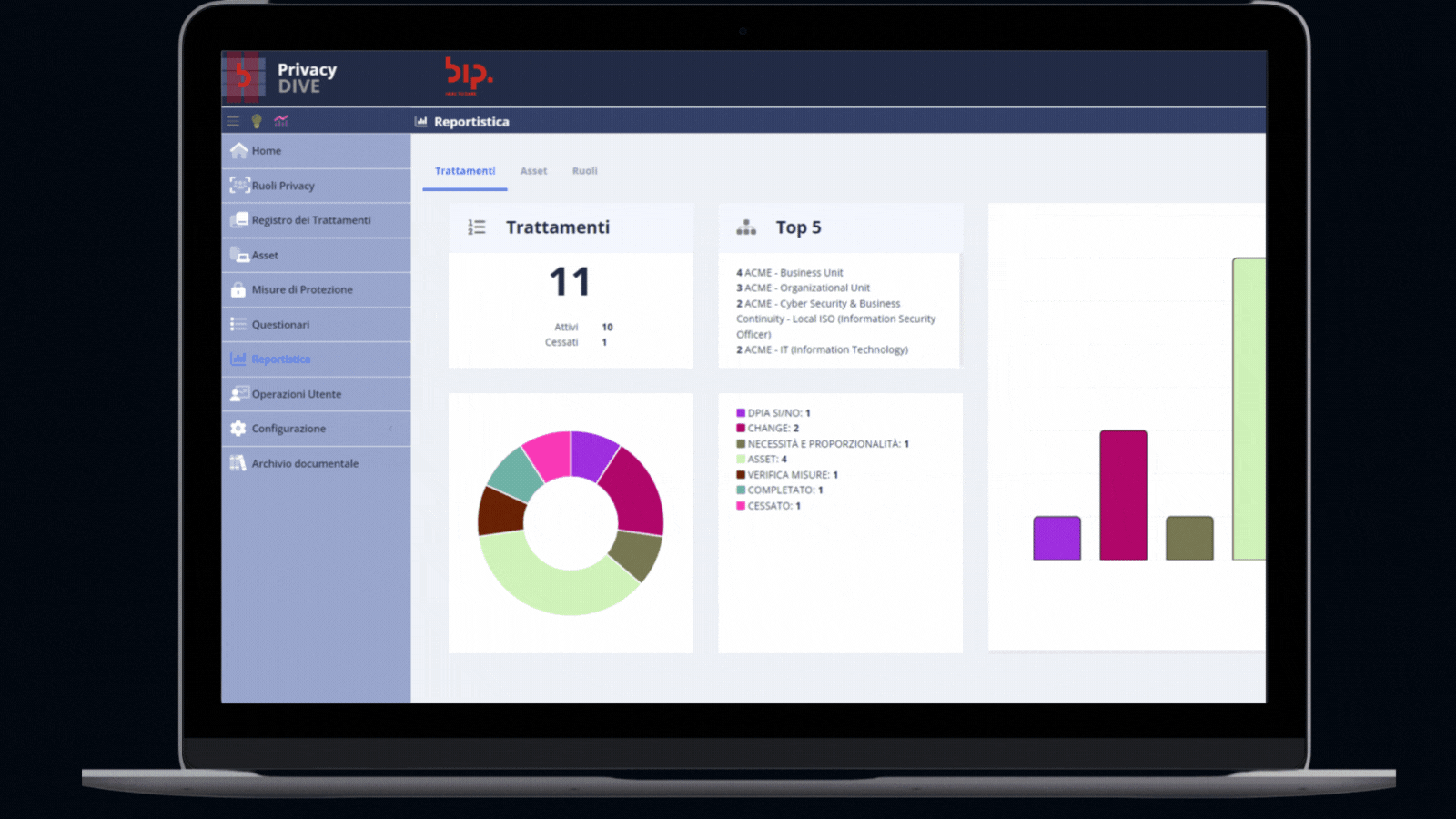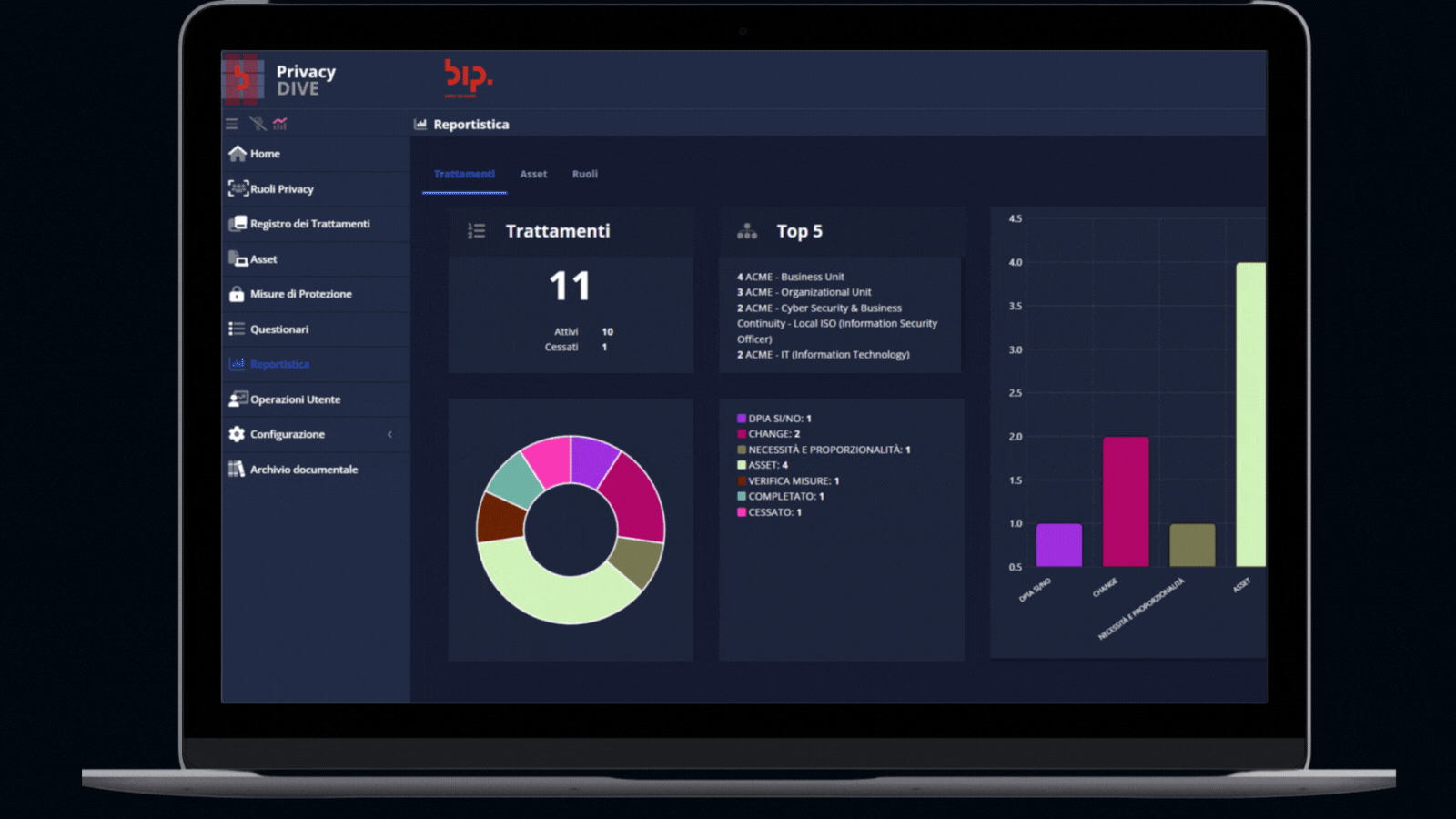
Getting a comprehensive view of the activities
This module supports advanced data analysis features, including graphs and statistics, for a comprehensive view of the activities recorded on the platform. It provides companies with comprehensive insights into their privacy compliance activities, enabling them to make informed decisions.
Data Breach Module
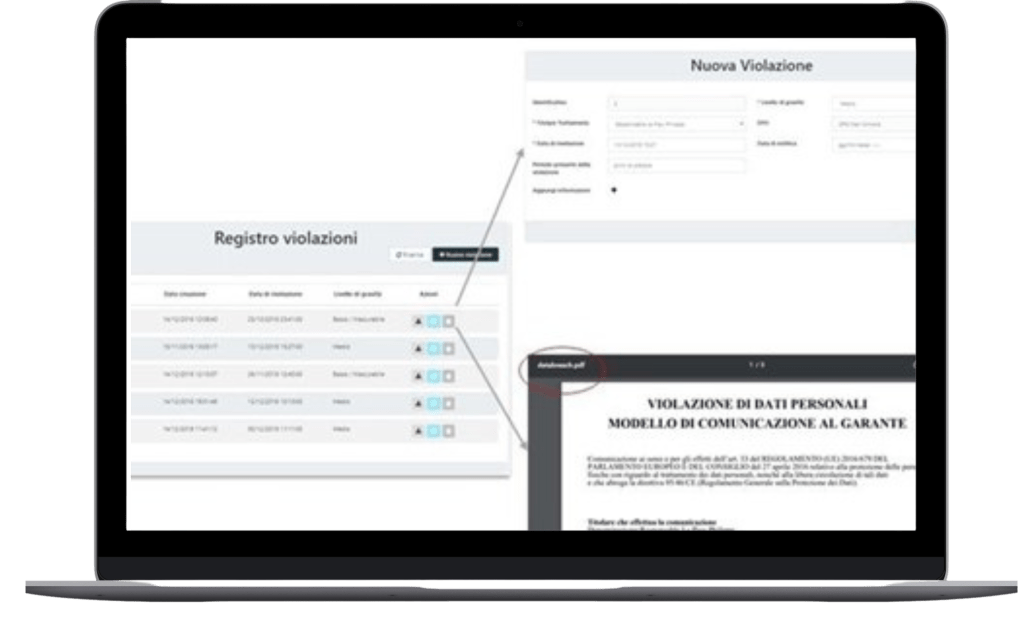
Manage personal data violations
An additional beneficial feature available on our platform is the pre-populated Data Breach communication template, in compliance with recommendations from the Supervisory authority (e.g., Italian Garante per la Protezione dei Dati Personali).
This extended module supports the impact assessment’s evaluation for data subjects, leveraging the automated mapping between the data breached and the related assets (e.g., File Shares, Storage Area Networks).
In a highly dynamic and rapidly evolving context, Privacy DIVE ensures the satisfaction of security and privacy standards. BIP’s commitment to information protection, operational effectiveness, and regulatory compliance is formally recognized by external entities through the attainment of Italian Certifications:
BIP is available to provide detailed documentation on this matter, demonstrating its commitment to ensuring the security and protection of sensitive information belonging to its clients.
In relation to the protection of personal data processed and the related protection techniques adopted as well as the security measures adopted in cloud environments, it is declared that:
- All users relating to cloud services can be requested from our Service Desk whose contacts are declared in the signed main contract.
- The encryption used for https communication uses the TLS 1.3 protocol. The backup is encrypted and saved in a data center different from that of the production servers, located at least 300 km away from each other.
- BIP is also available to provide all the support to allow the customer to implement their own cryptographic techniques if compatibility is permitted and security is guaranteed with the technology of pre-existing services.
- The methods of managing security incidents for SaaS and cloud environment uses divide responsibilities as follows: the cloud service user opens a ticket to our Service Desk service (see above) which takes the incident into management, proceeds with the resolution and notifies the customer of the results.
- BIP is subject to independent third-party audits on the compliance of the provision of cloud services with both the applicable mandatory legislation and the requirements of standards 27001: 27017 and 27018 for which it is certified. The certificates are published on this page, in the “Certifications” section
- The data centers used in the cloud services are AWS with data resident in the European community.
- All personal data relating to cloud services will be made available for a further period of 30 days from the date of termination of the service or contract, after which they will be deleted from the primary servers. Backup copies will be deleted starting from the thirtieth day after the end of the service. The period for deleting backup copies will last an additional five weeks.
- With reference to the services provided, BIP is responsible for the security of the logical infrastructure, while the customer is responsible for the correct use of the credentials assigned for the use of the services and for reporting any security events that may impact the service.
- Customer data managed in cloud services is subject to continuous incremental daily backup policies with five-week retention. Restore tests are carried out periodically on the data in environments with the same levels of protection as the production ones in order to verify the correctness of the backup process. At the end of the restore checks, they are deleted. The results of the restore tests are recorded in a special register.
- In the case of technical vulnerabilities that impact the services provided in the cloud, BIP undertakes to promptly implement the updates recommended by the suppliers of the vulnerable software. In the case of Vulnerability Assessment, the results and the remediation plan are shared with the customer.
- By way of example and not exhaustively, the security measures that BIP adopts in the provision of SaaS services are:
-
- Use of AWS, Cloud Service Provider Leader on the market at least TIER 3 in possession of ISO/IEC 27001, ISO/IEC 27017, ISO/IEC 27018 certifications.
- Logical protection of cloud environments with system isolation
- Secure deletion of virtual environments and non-reuse of resources allocated to individual instances.
- Continuously updated anti-malware measures
- Carrying out Vulnerability Assessment and Penetration Test at each major release, using a mirror copy of the production instance so as not to generate disruption.
Are you interested?
Fill in the form and you’ll be contacted by our experts!



