Do you want to speed up your response to cyber attacks?
Do you know how cyber threats are impacting your company’s business?
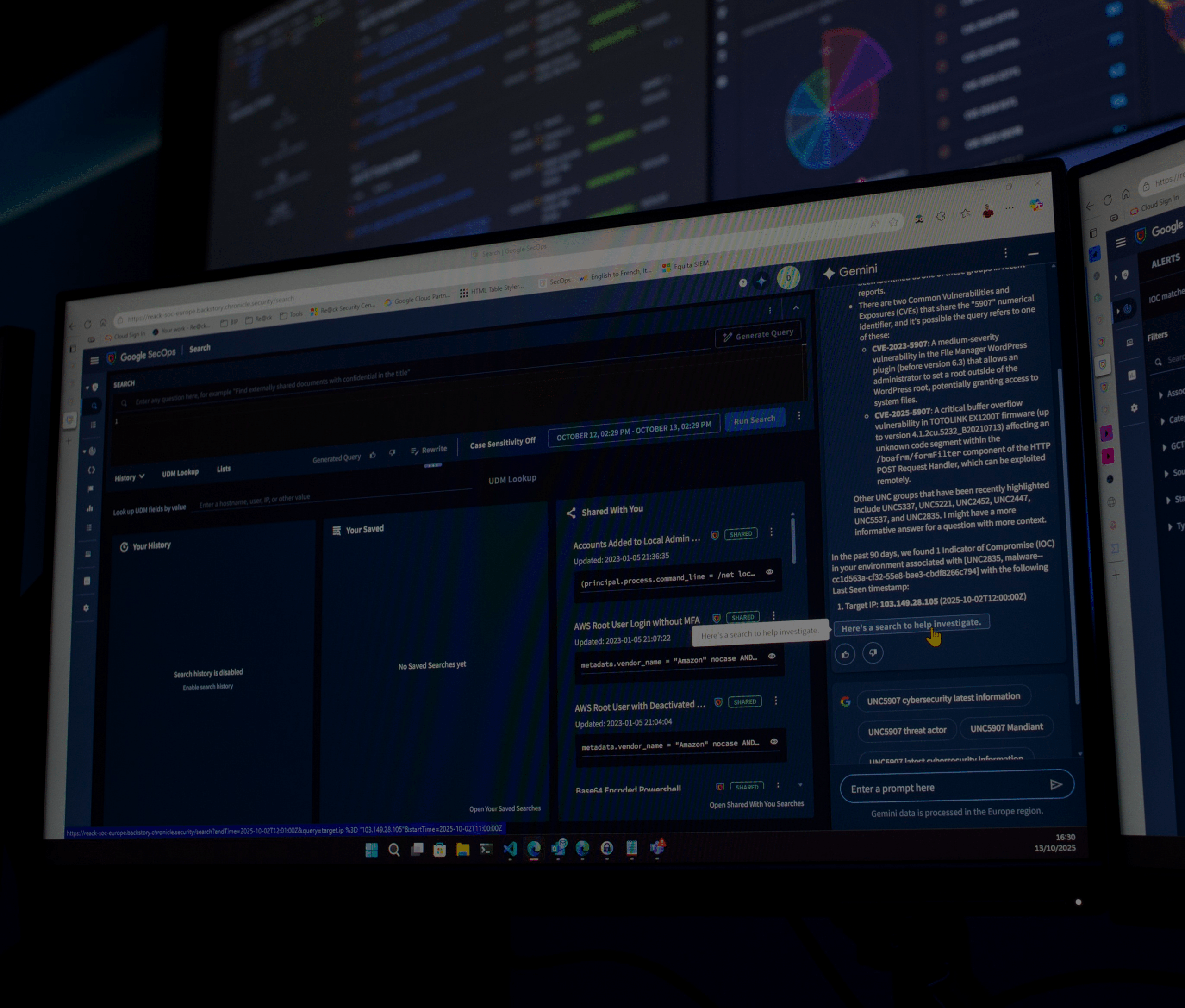
Whereas a typical SOC relies on time-consuming human analysis, the Reack Security Center combines BIP CyberSec’s DNA with Google SecOps technology to reduce Customers overload on investigation and information collection, and it implements a detection rule catalogue defined according to Customer’s actual cyber risks.
OUR APPROACH

After a decade of security advising organisations which operate in all the main sectors, we are facing a change in the top management’s perception of cybersecurity threats. We know how to effectively mitigate cybersecurity risks, so we wondered how we can respond to these new expectations.
KEY FEATURES & DIFFERENTIATORS OF OUR SOC
Transform your Security Operations team’s potential by unleashing the power of your people, processes, and technologies to drive unparallel influence throughout your organization.
KEY SERVICES AT A GLANCE
Get ready to elevate your team with BIP CyberSec top-notch managed services.
Monitor & Detect
Continuous monitoring of security telemetries and the detection of security events
- Log Monitoring
- Event Detection
- Security Triage


Respond
Containment of security incidents and recovery operations, focusing on “don’t’ leave the customer alone”
- Security Alerting
- Incident Escalation & Response
- War Room & Digital Forensics
Threat Intelligence
Proactive collection and analysis of open, deep, and dark web to identify potential new threats for the Customers
- IoC Management
- Data & credential leak
- Anti-phishing and brand monitoring
- Attack surface monitoring

Security Management
Maximize detection on «known» attacks and minimize the “noise” generated by false positives
- Detection Rules management
- Playbook Management
- Security Device Management
Service Governance & Reporting
Provide security operation trends and results to main stakeholders and constantly monitor the overall company risk exposure
- Business Reporting
- SLA Monitoring
- Service Review & Improvement


Vulnerability Management
Implement and maintain a vulnerability management program providing continuous VA, targeted PT and ad-hoc Red Teaming exercize
- Early warning
- Vulnerability assessment
- Penetration testing
- Red Teaming exercize
THE ARCHITECTURE
BIP Reack Security Center’s architecture is based on three integrated modules (Monitoring, Management & Intelligence Engines) which guarantee best-in-class technology stack and BIP CyberSec cybersecurity expertise.


MONITORING ENGINE
- Chronicle SIEM
- Chronicle SOAR
- Ticketing systems
- Reporting, dashboard and KPI
MANAGEMENT ENGINE
- Playbook management
- API management
- Vulnerability management
- Authentication & Authorization

INTELLIGENCE ENGINE
- Early Warning
- Threat Intelligence & IoC
- Threat Hunting
The core of our architecture is Google SecOps SOAR platform. The extensive use of our SOAR allows us efficient enrichment of events, automize parts of incident response actions, and quick response to automated attacks
Detection rules, created based not only on standards, best practice and market services, but also on real cyber security risks of the Organization
Are you interested?
Get in touch with our specialists to catch our Reack Security Center in action!
Get in touch with our specialists to catch our Reack Security Center in action!

© 2022 – Business Integration Partners S.p.A. | CyberSec Practice – VAT: 03976470967
Headquarters
Torre Liberty Building
Galleria de Cristoforis 1, Milan, 20121
Italy
Registered Office
San Babila
Piazza San Babila 5, Milan, 20122
Italy